- Home
- Solutions
- Solutions of Cloud Services
- Security Acceleration Solution
Security Acceleration Solution
Solution Introduction
proactively defends against security threats from both the network and application layers, comprehensively improving website security posture and operational efficiency.

Solution Features
Global High-Speed Access
With over 2800 nodes covering more than 70 countries and regions, it combines technologies such as dynamic and static separation, private protocols, and smart routing to achieve efficient transmission across the entire network.
Full-Site Security Protection
Aggregates DDoS cloud scrubbing, Web attack protection, business security, and API security, achieving comprehensive stack protection covering layers L3-L7.
Full Lifecycle Risk Management
Based on the entire process before, during, and after an event, by Asset Discovery → Strategy Deployment → Systematic Operation, a complete risk management cycle is achieved.
Industry-Tailored Customization
Full-path intelligent distribution, combining dynamic and static separation, private protocols, and smart routing to achieve efficient transmission across the entire network.
High Availability Architecture
Global massive resources, easily handling sudden increases in business and unexpected attacks; global load balancing, avoiding single points of failure, more reliable.
Solution Features
 Cloud Deployment
Cloud Deployment
One-click access, zero modification to existing infrastructure, expert 24/7 online support, instant problem resolution.
 Global Acceleration
Global Acceleration
Dynamic-static content intelligent separation, smart routing, protocol optimization, and other technologies achieve efficient content transmission.
- Dynamic-static Intelligent Separation: Intelligent distributed caching for static content, dynamically selecting the optimal route for sourcing.
- Intelligent Routing: Real-time detection of network link quality across the entire network, selecting the optimal path to achieve smooth cross-network access.
- Protocol Optimization: Utilizing proprietary developed private transmission protocols to achieve stable and rapid data transmission.
 Data transmission guarantee
Data transmission guarantee
Full support for HTTP2.0, supporting content anti-hijacking and various anti-leeching methods.
- HTTPS Acceleration: Fully supports HTTP2.0, SNI shared IP, multi-certificate format, and no private key scheme.
- Content Anti-Hijacking: Prevents hijacking and handles hijacking through URL encryption, dynamic feature value validation, MD5 validation, etc.
- Supports various anti-leeching methods: Referer anti-leeching, Cookie anti-leeching, IP access control, etc.
 Risk Management
Risk Management
In the pre-incident phase, combined with security expert services, identify and mitigate web application security risks.
- Vulnerability Scanning: Conduct security scans on web application assets using vulnerability scanners to discover security vulnerabilities (OWASP TOP10, weak passwords, CVE vulnerabilities, etc.) in web applications.
- Penetration Testing: Deploy security experts to conduct non-destructive vulnerability exploration from a hacker's perspective on target systems, checking potential security risks in the target systems.
- Internet Exposure Asset Discovery: Provide internet asset discovery, identification, monitoring, auditing, etc. services through platform and manual services, including comprehensive queries and correlation analysis of function variable names, IPs, and keywords to discover, identify, monitor, audit, etc. internet assets and explain user discovery and inventory of internet assets.
- API Asset Inventory: Explain the discovery of API businesses not yet grasped by enterprises from traffic data, form an API asset list, and conduct asset inventory for subsequent protection work based on traffic analysis.
- Intelligent Protection Strategy: Automatically adapt protection strategies based on intelligent analysis of customer business on the platform, achieving out-of-the-box use.
- Security Training: Provide information security training services focusing on improving security awareness while also enhancing security technical capabilities.
 L3/L7 Full-Site Protection
L3/L7 Full-Site Protection
In the mid-incident phase, provide comprehensive security protection for web applications from the perspectives of network security, application security, business security, and API security.
- DDoS Protection: Real-time cleaning of network layer DDoS attacks at the edge using second-level detection patented technology.
- CC Protection: Achieve second-level detection and defense against application layer CC attacks based on AI traffic behavior analysis technology.
- Business Security: Provide lightweight information anti-crawling and scenario-based risk control capabilities for business aspects.
- API Security: Provide fine-grained management and protection for API applications to avoid API abuse and prevent data leakage.
- Web Attack Protection: Cover various Web attack protections under OWASP Top10, provide flexible protection and massive IP banning based on CDN's distributed computing power, and support joint decision-making with local protection of the origin site to improve defense accuracy.
- Full-Site Isolation: Use remote browsing isolation technology to make the website's original code invisible, actively hide the website's attack surface, and combine technologies such as obfuscating access paths and encrypting interactive content to effectively mask 0day vulnerability attacks.
- Collaborative Protection: Manage the security policies of various protection modules at network layers L3-L7 through the full-site protection management platform, and form true depth protection through data aggregation and intelligence collaboration to simplify operational work and further enhance overall security protection.
 Security Operations
Security Operations
In the post-incident phase, with the goal of reducing risks, provide systematic security operational capabilities and solidify full-chain risk management.
- Comprehensive Security Posture: Aggregate data from various protection modules and present them in a concise, business-friendly format, providing an overview of web security posture and proactively perceiving and responding to known security incidents.
- Continuously Optimized Hosting Strategies: Provide higher-quality protection rules and strategy suggestions, optimize business protection strategies, and maintain continuous defense against black industry by combining platform practical combat experience, continuous offensive and defensive research, and combat results.
- Security Expert Operations: Senior security experts can also provide specialized security services such as security training and heavy protection services, while continuously monitoring and managing client risks.
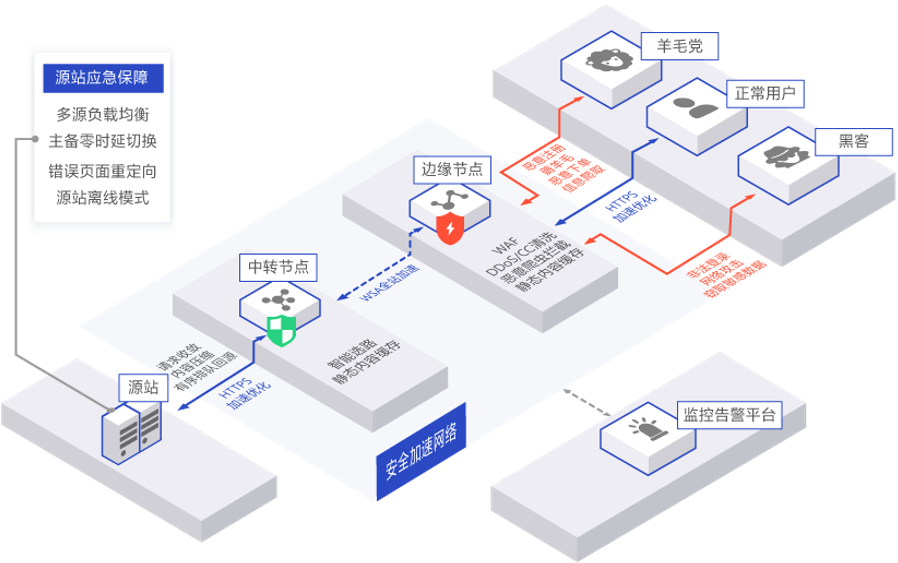
Solution Architecture
Architecture Features
24小時專業工程師維護。
High reliability, stability,and security of the global network,
24-hours professional engineering maintenance.
